Maximum Validity For Certificates
You can configure expiration period for Certification Template. By default there are default maximum validation periods set to:
-
One year for Stand-alone Certification Authority
- Two years for Enterprise Certification Authority
This means you have Certification Template set its validity for example for 10 years, but you can enroll certificates with validity 1 or 2 years (Stand-alone / Enterprise Certification Authority).
This can be changed via registry keys described in KB254632.
Thank you for my colleague Róbert Švec.
Quickie: Remove Domain Controller role from Exchange 2007 server
Last night I removed Domain Controller Role from Exchange 2007 server and we had problem in the morning with Exchange Outlook Web Access (OWA). We couldn’t log in at all. Symptomps:
- Form based authentification was enabled, but Basic was proposed to clients instead
- When users logged in they received 440 Login Timeout error
After couple minutes of googling I found this article which solved problem.
IMHO when computer was demoted from domain controller role it created local SAM database and didn’t use domain created accounts IUSR_ComputerName and IWAM_ComputerName.
Disable Exclusive Rights for roaming profiles
When administrators implement Roaming Profiles they define folder where roaming profile should be stored on fileserver. By default file permissions for the newly generated profile are full control for the user, full control to SYSTEM and no file access for the administrators group. You can not access this profiles with administrator account and clean it up. First you had to take ownership and then you can change ACL, but this is not what you want, because owner should be user.
You can fix this in two steps:
New roaming profile folders
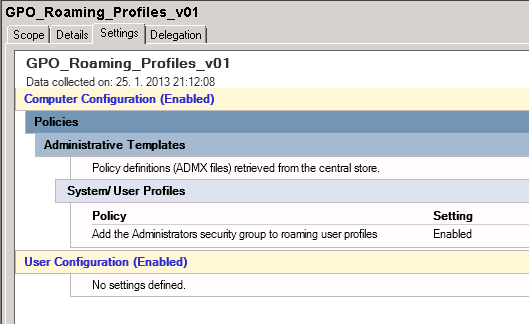
You can change default behaviour on new profile folder creation. It can be changed by applying GPO to domain controllers with following setting Enabled:
Change ACLs for existing profile folders
This will be in couple steps:
-
Download SubInACL.exe
- Download PsExec
- Log into fileserver where profiles are stored
- Run cmd.exe under SYSTEM account by running command
psexec -sid cmd.exe
- In new cmd.exe window go into directory where roaming profiles are stored. For example: cd G:\Profiles\
- Add BUILTIN\Administrators into ACLs of roaming profiles by running following command:
subinacl /subdirectories=directoriesonly G:\Profiles\*.* /GRANT=Administrators=F
Enjoy accessible roaming profile folders 🙂
Quickie: GPO Preferences variables
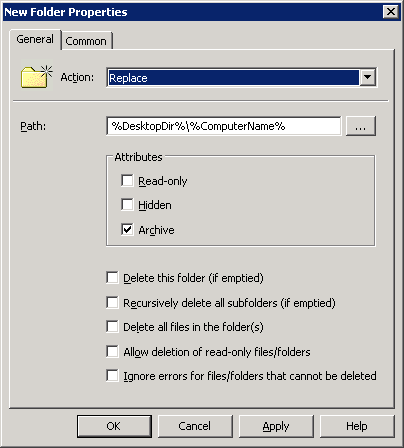
When you want to use system variables in GPO Preferences you can do so. For example: if you want to create folder on user’s desktop called as computer name, you can use variable in New Folder Properties:
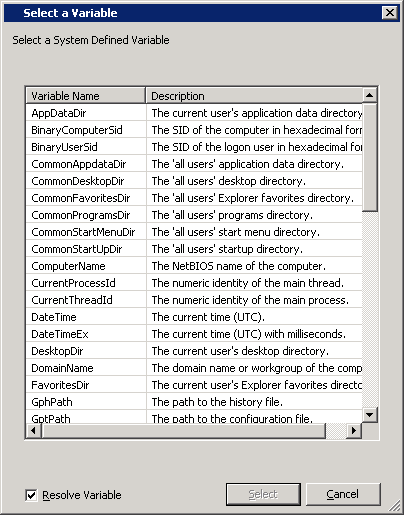
If you don’t know what variables you are able to use in Preferences input fields you can press F3 and it will display you a list of variables you can use:
I just found info at Microsoft.
DFS Problem in multi domain environment
Couple months ago we have created Active Directory domain for one of our customer. His AD was subdomain of existing AD domain hosted in Germany. Let’s call them following:
- DOMAIN.LOCAL <– Main AD in Germany
- SK.DOMAIN.LOCAL <– New created domain in Slovakia
To make administrators life easier in future, we have created DFS Shares in domain SK.DOMAIN.LOCAL. One of those DFS shares is called “Common”. So people in Slovakia were accessing DFS share \\\\SK.DOMAIN.LOCAL\\Common and share data. Under this DFS Namespace following share was hidden \\\\FSSERVER\\Common.
Everything worked just fine.
Problem
Problem appeared when users from Germany (from domain DOMAIN.LOCAL) wanted to access this share. There were following symptomps:
-
Users from DOMAIN.LOCAL couldn’t access \\\\SK.DOMAIN.LOCAL\\Common
- Users from SK.DOMAIN.LOCAL could access \\\\SK.DOMAIN.LOCAL\\Common
- Users from DOMAIN.LOCAL could access \\\\SK.DOMAIN.LOCAL\SYSVOL and \\\\SK.DOMAIN.LOCAL\NETLOGON
There were no firewalls between two domains. All ports were accessible.
Solution
After couple tries (and using dfsutil) I figured out that client machine from DOMAIN.LOCAL get as DFS Refferal NetBIOS server name FSSERVER and it cannot translate FSSERVER to IP (FSSERVER is from SK.DOMAIN.LOCAL). Client machine from DOMAIN.LOCAL although can translate FQDN of FSSERVER.SK.DOMAIN.LOCAL. I tried to put FSSERVER IP record into client machine’s hosts file and everything started to work perfectly. So we have more solutions to solve issue:
-
Synchronize NetBIOS names between two domain (weird)
- Add DNS Search suffixes to clients in domain (not nice solution and can slowdown DNS queries)
- Force DFS to propagate FQDN as refferals (winner)
I decided to force DFS to propagate FQDN as refferals. It’s made by change in registry keys for DFS service. More about it is at http://support.microsoft.com/kb/244380/en-us. One more important thing is that you need to remove and re-add refferal servers from DFS Namespaces. I used DFS console because I didn’t use DFS Replication. If you do use DFS Replication it’s recommended to do it using cmd line (dfscmd.exe).
That’s all folks,
Quickie: Service Accounts description
More often I see people (IT admins) not understand differences between Local Service Accounts so I decided to write more about it:
SYSTEM
This account has full access to local computer. It can access network resources with rights (account) of the computer. This account has full access to domain it self when used on Domain Controller.
LOCAL SERVICE
This account has same right as local Users group. It goes to network as annonymous user (null session).
NETWORK SERVICE
It’s almost same as LOCAL SERVICE. Only difference is that it uses computer account to access network resources.
Quickie: Exchange Empty Submission queue
Today I was solving problem with open relay Exchange server. I came to server and it was full of SPAM e-mail messages. I needed to clean all this mess from Submission queue. I used following command:
Get-Message -Filter {FromAddress -eq “<>”} -Server MAILSERVER | Remove-Message
That’s all folks 🙂
DNS records for domain controller
I always was wondering if there is any way to determine all DNS records NetLogon service registers in DNS server. This record list is located at %systemroot%\\system32\\config\\netlogon.dns.
_ldap._tcp.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.Site1._sites.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.gc._msdcs.domain.local. 600 IN SRV 0 100 3268 SERVER-DC1.domain.local. _ldap._tcp.Site1._sites.gc._msdcs.domain.local. 600 IN SRV 0 100 3268 SERVER-DC1.domain.local. _ldap._tcp.cb30fef3-1c01-46c1-951a-5dec33f85833.domains._msdcs.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. bcb148b0-c836-4847-bd55-3d3991821f76._msdcs.domain.local. 600 IN CNAME SERVER-DC1.domain.local. _ldap._tcp.dc._msdcs.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.Site1._sites.dc._msdcs.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _gc._tcp.domain.local. 600 IN SRV 0 100 3268 SERVER-DC1.domain.local. _gc._tcp.Site1._sites.domain.local. 600 IN SRV 0 100 3268 SERVER-DC1.domain.local. _ldap._tcp.ForestDnsZones.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.Site1._sites.ForestDnsZones.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.DomainDnsZones.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.Site1._sites.DomainDnsZones.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. _ldap._tcp.pdc._msdcs.domain.local. 600 IN SRV 0 100 389 SERVER-DC1.domain.local. domain.local. 600 IN A 10.0.0.22 gc._msdcs.domain.local. 600 IN A 10.0.0.22 ForestDnsZones.domain.local. 600 IN A 10.0.0.22 DomainDnsZones.domain.local. 600 IN A 10.0.0.22 _kerberos._tcp.dc._msdcs.domain.local. 600 IN SRV 0 100 88 SERVER-DC1.domain.local. _kerberos._tcp.Site1._sites.dc._msdcs.domain.local. 600 IN SRV 0 100 88 SERVER-DC1.domain.local. _kerberos._tcp.domain.local. 600 IN SRV 0 100 88 SERVER-DC1.domain.local. _kerberos._tcp.Site1._sites.domain.local. 600 IN SRV 0 100 88 SERVER-DC1.domain.local. _kerberos._udp.domain.local. 600 IN SRV 0 100 88 SERVER-DC1.domain.local. _kpasswd._tcp.domain.local. 600 IN SRV 0 100 464 SERVER-DC1.domain.local. _kpasswd._udp.domain.local. 600 IN SRV 0 100 464 SERVER-DC1.domain.local.
This list can be used to import all required DNS records into DNS servers that don’t support dynamic updates.
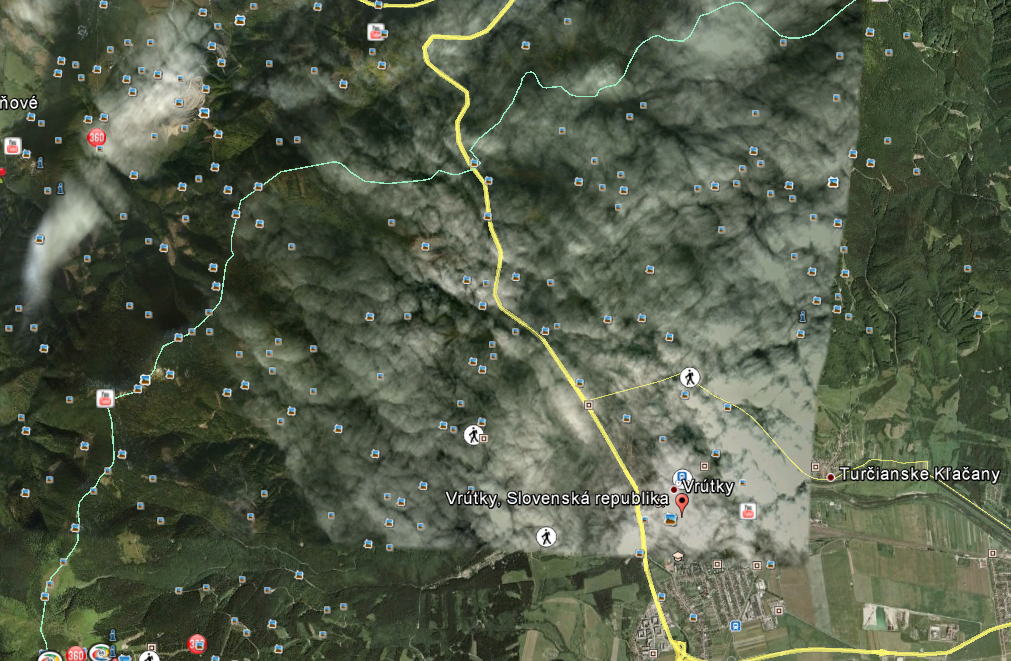
Vrutky v oblakoch
Dneska som sa nieco chcel pozriet nieco vo Vrutkach na google maps a zistil som, ze cele Vrutky su pod oblakmi 🙂
Dakujeme Google 🙂
Recent Comments