You can configure expiration period for Certification Template. By default there are default maximum validation periods set to:
This means you have Certification Template set its validity for example for 10 years, but you can enroll certificates with validity 1 or 2 years (Stand-alone / Enterprise Certification Authority).
This can be changed via registry keys described in KB254632.
Thank you for my colleague Róbert Švec.
When administrators implement Roaming Profiles they define folder where roaming profile should be stored on fileserver. By default file permissions for the newly generated profile are full control for the user, full control to SYSTEM and no file access for the administrators group. You can not access this profiles with administrator account and clean it up. First you had to take ownership and then you can change ACL, but this is not what you want, because owner should be user.
You can fix this in two steps:
New roaming profile folders
You can change default behaviour on new profile folder creation. It can be changed by applying GPO to domain controllers with following setting Enabled:
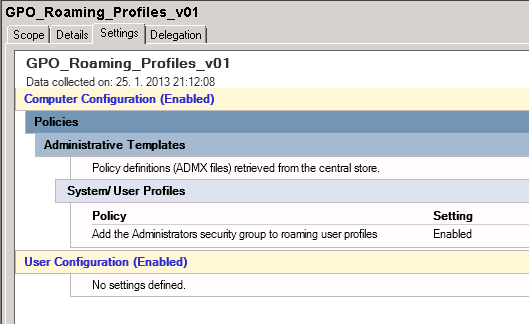
Change ACLs for existing profile folders
This will be in couple steps:
-
- Download PsExec
- Log into fileserver where profiles are stored
- Run cmd.exe under SYSTEM account by running command
psexec -sid cmd.exe
- In new cmd.exe window go into directory where roaming profiles are stored. For example: cd G:\Profiles\
- Add BUILTIN\Administrators into ACLs of roaming profiles by running following command:
subinacl /subdirectories=directoriesonly G:\Profiles\*.* /GRANT=Administrators=F
Enjoy accessible roaming profile folders 🙂
More often I see people (IT admins) not understand differences between Local Service Accounts so I decided to write more about it:
SYSTEM
This account has full access to local computer. It can access network resources with rights (account) of the computer. This account has full access to domain it self when used on Domain Controller.
LOCAL SERVICE
This account has same right as local Users group. It goes to network as annonymous user (null session).
NETWORK SERVICE
It’s almost same as LOCAL SERVICE. Only difference is that it uses computer account to access network resources.
Just a quick image about differences between “old” Software Restricion Policy and “new” AppLocker:
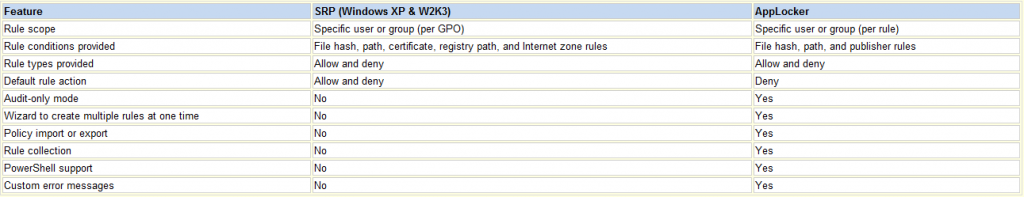
Now it’s easy to describe and remember.
Three days ago I installed Internet Explore 10.0 on my Windows 7 SP1. I downloaded it from here.
Internet Explorer 10
After couple seconds I found out only little changes. Design of buttons changes little bit. Also design of check boxes.
After couple minutes I found following new things:
Text box change
Now you can delete content of text box in one click. Clicking by X on the end of the box:
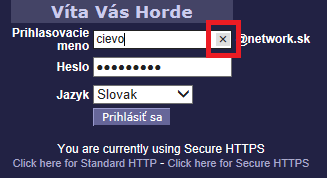
Delete text box
Password box change
On password box you can see what’s under stars:
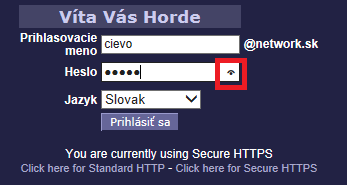
Hidden password in box
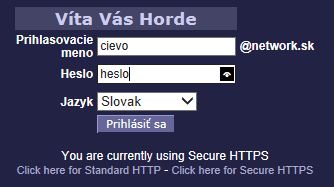
Show password in box
Easy copy and paste
When you select text and pictures in IE 10.0, you can drag and drop it into some application (e.g. Word, Outlook, …). This is very neat and cool.
Faster
My personal feeling is that webpages are displayed much faster than before, but this can be just feeling 🙂
When I upgraded from ISA 2006 to TMG 2010 I found some special problem. There was HQ with TMG 2010 and one branch with ASA 5505. Between those two location there was Site to Site VPN tunnel created. Everything worked fine, beside one problem. Users in branch couldn’t access anything on TMG server. They couldn’t ping it or do anything with it. They couldn’t browse Internet, because TMG was also web proxy server for them.
Read more…
Categories: Computer network, Microsoft, Security Tags: 0xc0360007, 2502685, drop, forefront, ipsec, microsoft, packet, site to site, STATUS_IPSEC_CLEAR_TEXT_DROP, tmg 2010, vpn
Customer wanted to upgrade his ISA 2006 server to “new” TMG 2010. I thought it would be nice and easy process. It could be if there were no problems which I didn’t expect to be a problem in “new” software. Old server was still functional and I wanted to prepare new server and migrate all settings and certificates.
Requirements
To install all requirements you can install required packages by yourself or you can use Run Preparation Tool from installation screen of TMG. Why didn’t they include it into installation package it self?
Messed up console
When I was done with installation I ran TMG console and I received following error:
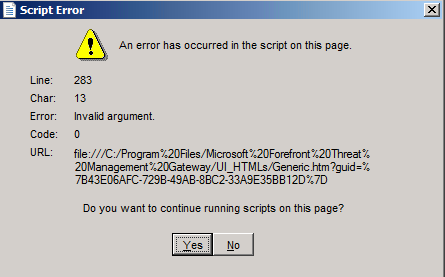
Read more…
Regarding to official blog article from Directory Service Team MaxTokenSize for Access Token tickets, which is four times more than before.
Today my ex-colleague called me that Windows 2000 Active Directory domain, he is taking care of, is not fully functional. He mentioned that “primary” domain controller is dead and now domain has some problems.
I had to seize all FSMO roles to live Domain Controller using ntdsutils as mentioned at this Microsoft article:
http://support.microsoft.com/kb/255504
I manually deleted dead domain controller’s information from Active Directory using following Microsoft article:
http://support.microsoft.com/kb/216498
After checking events I found out that there was also Certification Authority on dead domain controller and I needed to clean up all Enterprise Domain Certification Autorhority information from Active Directory Domain using following Microsoft article:
http://support.microsoft.com/kb/555151
PS: Don’t forget to put your account into all “administrative” groups: Domain Admins, Enterprise Admins and Schem Admins.
Once upon the time I played with enterprise certification authority at one of our customers. I’ve created new certificate for certification authority. And then problem begun.
Read more…







Recent Comments