Certification Authority – decrease key lenght
One my colleague wanted to make one of our customer’s environment very secure so he decided to install Enterprise Certification Authority environment with 4kB keys. He created one offline root CA with 4kB key (Windows 2003). This computer is offline all the time. Another CA is Issuing CA which key is signed by root CA. This issuing CA also had 4kB key (Windows 2008 R2). Certificates issued by issuing CA were from 2kB-16kB.
Problem raised when customer wanted to create certificate for Cisco devices to secure Wifi. To make those devices use and trust certificates from issuing CA customer needed to import Root and Issuing CA public certificates into those Cisco devices. And this was a problem. Those Cisco devices didn’t want to work with more than 2kB certificates.
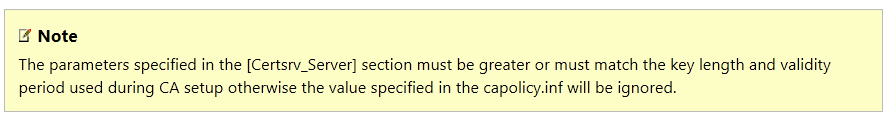
Now there were two solutions. One was to create new Enterprise CA Root and also Issuing CA with 2kB and reissue all certificates. When you browse official Microsoft documentation you can find information that key lenght (size) can be equal or greater:
When I played in my lab I found out that I’m able to change it to lower lenght and it works regardless on official Microsoft documentation.
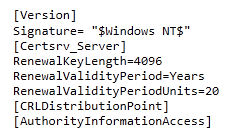
When you want to decrease key lenght you need to request new CA certificate with custom attributes. To make custom attributes you need to create file CAPolicy.inf and add it into C:\Windows directory. Basic CAPolicy.inf file can look as following:
Where you define key lenght with parameter RenewalKeyLenght. Which should be set to 2048 when you want 2kB key.
First you need to Request for new certificate on the highest CA in CA’s hierarchy. In my scenario that was Enterprise Root CA. When I requested for new CA certificate it was generated with 2kB key lenght. So now all certificates signed by Enterprise Root CA whould be signed with new 2kB key and all old certificates will be still trusted – until validity of old 4kB certificate. Next step was to make same thing to Issuing CA – create CAPolicy.inf file and request renewal of CA certificate. Now all certificates issued by Issuing CA would have certificate chain made from 2kB Root CA and 2kB Issuing CA.
After all you have following situation:
-
all old certificates signed by 4kB Root and 4kB Issuing CAs would be valid until validity of those two CAs
-
all new certificates are signed by 2kB Root and 2kB Issuing CAs
-
now I can import Root and Issuing CAs’ certificates into Cisco devices and create new certificates which are trusted by those Cisco devices
So never trust public official documentation from Microsoft. Just try to solve problem your way – of course test it in lab prior in production 🙂
Recent Comments